Cybersecurity remains an alarming concern in today’s web-reliant environment. Threats ranging from data breaches to ransomware attacks require organizations to implement extensive defense strategies.
According to a report from CyberSecurity Ventures, cybercrime is expected to cost the globe $9.5 trillion in 2024. Traditional security measures like firewalls and antivirus software are no longer sufficient, requiring proactive approaches involving continuous digital footprint monitoring.
A website breach or attack can lead to financial loss, reputational damage, and legal ramifications. Safeguarding websites against cyber threats is fundamental to risk management and maintaining customer trust.
Log monitoring is a powerful tool that strengthens cybersecurity measures and protects against potential threats. At its core, log monitoring involves collecting and interpreting log data generated by systems and applications. These logs contain user activities, system events, and network traffic information.
By monitoring and analyzing these logs in real time, organizations can detect suspicious behavior, identify security incidents, and respond proactively to potential threats.

This guide explores the significance of log monitoring and its role in bolstering online security.
Detecting Cybersecurity Threats Through Log Monitoring
Monitoring log data for suspicious activities allows organizations to identify potential security breaches. It enables companies to handle events such as unauthorized access to sensitive files or abnormal network traffic that require immediate attention.
By evaluating information from different log sources, such as authentication logs, firewall logs, and system logs, security teams can maintain a bird’s-eye view of their systems and take proactive measures to mitigate risks.
Log Monitoring for Incident Response and Mitigation
In the event of a security incident, logs allow security experts to investigate the root cause and assess the extent of the damage. By analyzing log data from the affected systems, security teams can reconstruct the events, identify the entry point of the attack, and determine the scope of the compromise.
This information is essential for containing the incident, restoring normal operations, and implementing corrective measures.
Cybersecurity Benefits of Effective Log Monitoring
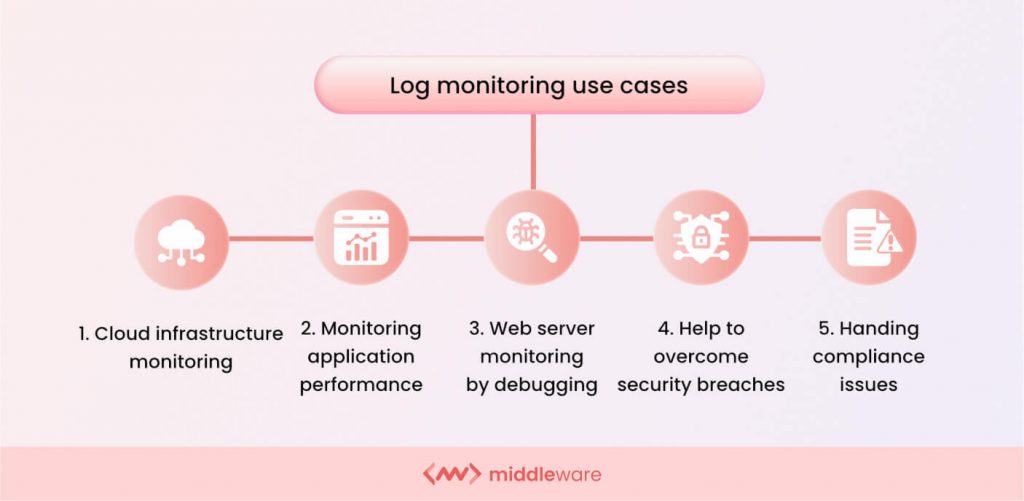
Effective log monitoring allows organizations to safeguard their digital assets and mitigate cyber risks. It provides the following benefits:
1. Early Threat Detection and Prevention
Organizations can identify potential threats early by monitoring logs for suspicious activities, such as unauthorized access attempts or abnormal user behavior.
This proactive approach enables security teams to investigate suspicious incidents and implement preventive measures to deal with attacks.
2. Enhanced Incident Responses
Log monitoring provides evidence and contextual information for incident investigations and root cause analysis. Security teams can reconstruct the sequence of events, determine the attack vector, and assess damage.
This insight helps incident response efforts and quickens the restoration of normal operations.
3. Improved Visibility
Monitoring logs across systems and applications can help organizations gain insights into user behavior, track access, and identify potential security violations.
This encourages accountability among users and administrators, enabling organizations to trace actions back to specific sources responsible for security incidents or compliance inconsistencies.
4. Regulation Compliance
Effective log monitoring provides audit trails and documentation of security controls.
By maintaining logs and conducting regular log analyses, organizations can demonstrate compliance with regulatory mandates, mitigate the risk of penalties, and uphold trust and confidence.
5. Proactive Risk Management
Log monitoring enables organizations to identify and mitigate security vulnerabilities before exploiting them. Organizations can proactively address security gaps and implement security controls by analyzing logs for indicators of compromise (IoCs), suspicious activities, or security policy violations.
This proactive approach minimizes the likelihood of security breaches and safeguards digital assets against threats and vulnerabilities.
6. Continuous Improvement and Optimization
Effective log monitoring enables continuous improvement of cybersecurity defenses through performance analysis and feedback loops. Analyzing log data for patterns and security incidents allows organizations to refine security procedures and optimize security controls against evolving cyber threats.
Organizations can adapt to new threats, learn from past incidents, and continuously enhance cybersecurity.
Best Practices For Cybersecurity Through Log Monitoring
To utilize the full potential of log monitoring, organizations should adhere to the following practices:
- Implement a centralized logging infrastructure to aggregate logs from different sources and establish a comprehensive analysis mechanism.
- Use automation and machine learning to streamline log analysis processes and threat detection.
- Review log monitoring policies and procedures to adapt to new cyber threats and regulatory requirements.
- Encourage effective communication between security teams and business operations to ensure alignment between security objectives and operational decisions.
- Implement access controls to restrict access to log data and ensure that only authorized personnel have permission to view, modify, or delete logs.
- Define log retention periods for different types of logs based on regulatory requirements, operational needs, and storage capacity.
- Implement log rotation mechanisms to archive older logs, compress log files, and free up storage space.
- Implement cryptographic hash functions or digital signatures to generate checksums or hashes of log files and compare them against baseline values to ensure data integrity.
- Integrate log monitoring with Security Information and Event Management (SIEM) solutions to centralize log management, correlation, and analysis.
Compliance with Data Protection Regulations
Non-compliance with data protection regulations can result in severe financial penalties and reputational damage.
To ensure compliance with data protection regulations, companies should consider the following:
- Implement log retention policies by regulations to ensure the retention of logs for the mandated timeframe.
- Encrypt sensitive log data to protect it from unauthorized access and mitigate breaches.
- Conduct regular audits to proactively validate adherence to regulatory requirements and resolve compliance gaps.
Creating a Robust Cybersecurity Strategy Using Log Analysis
By integrating log analysis into their cybersecurity strategy, organizations can:
- Establish a threat intelligence program to identify emerging cyber threats and prioritize their mitigation efforts.
- Regular security assessments and penetration testing must be conducted to identify vulnerabilities and ensure the effectiveness of security controls.
- Implement an incident response plan that outlines roles, responsibilities, and procedures for responding to security incidents.
Conclusion
Log monitoring offers organizations valuable insights into their digital frameworks and helps detect, resolve, and mitigate security threats effectively. By incorporating log monitoring into their cybersecurity protocols, organizations can protect against cyber attacks and safeguard the confidentiality and integrity of their data assets.
As cyber threats continue to evolve, organizations need to prioritize cybersecurity through effective log monitoring practices and stay one step ahead of malicious parties looking to exploit security vulnerabilities.
Author bio:
Ashwini Dave
Gravatar Mail id: ashwinidave94@gmail.com
Bio:
Ashwini Dave is an accomplished digital marketer specializing in SEO and groundbreaking campaigns. With an MBA in Marketing, she crafts strategic, high-impact results. A tech enthusiast exploring AI and cutting-edge tech, Ashwini seamlessly integrates innovation into her marketing strategies. Outside the digital sphere, she is an avid traveler, finding inspiration in nature’s beauty while exploring the world.

